Version 2.5.0 - 2/23/2022
# Version 2.5.0 - 2/23/2022
In this release we added the ability to assume a role to view your system. This is a really helpful feature for those of you that are using role based authentication. We are still barreling down on our version 3.0 release. But continue to strive to make Commandeer better for everyone.
# Assume Role
The concept of assuming a role in AWS is pretty straightforward. You as a developer will have your IAM user with access keys, but this user will not have access to any resources. Your sysadmin will then give you access to different roles in the system. For instance, you might get access to a lambda role that allows you to view lambdas and the services they talk to like S3 or DynamoDB.
Your main user access keys need to be setup in the .aws/credentials file, and then the roles are in the .aws/config file. You can see an example of this below.
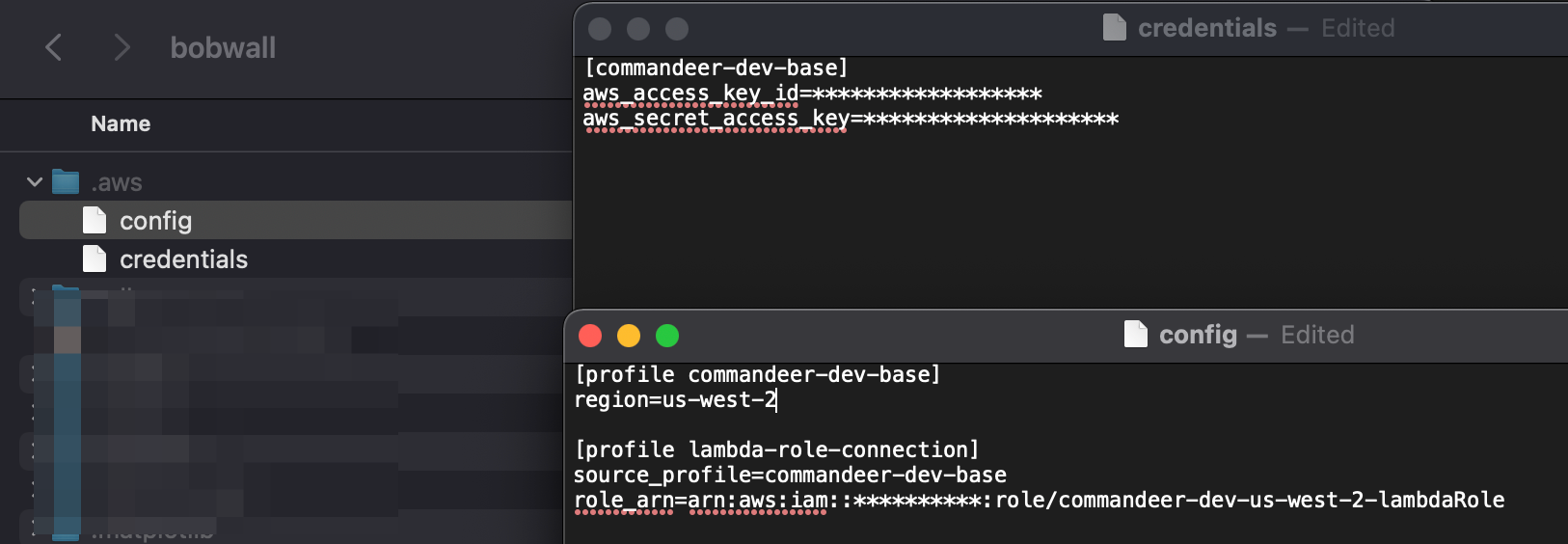
The top is the keys that will be used to assume the role, your user keys. In the bottom section, you can see that there is a lambda-role-connection profile. This has a reference to commandeer-dev-base via the source_profile. It also contains the role__arn of the role you would like to assume.
In Commandeer, when you create an account to connect to your system, you will be able to select these. Below you can see the Edit Account dialog.
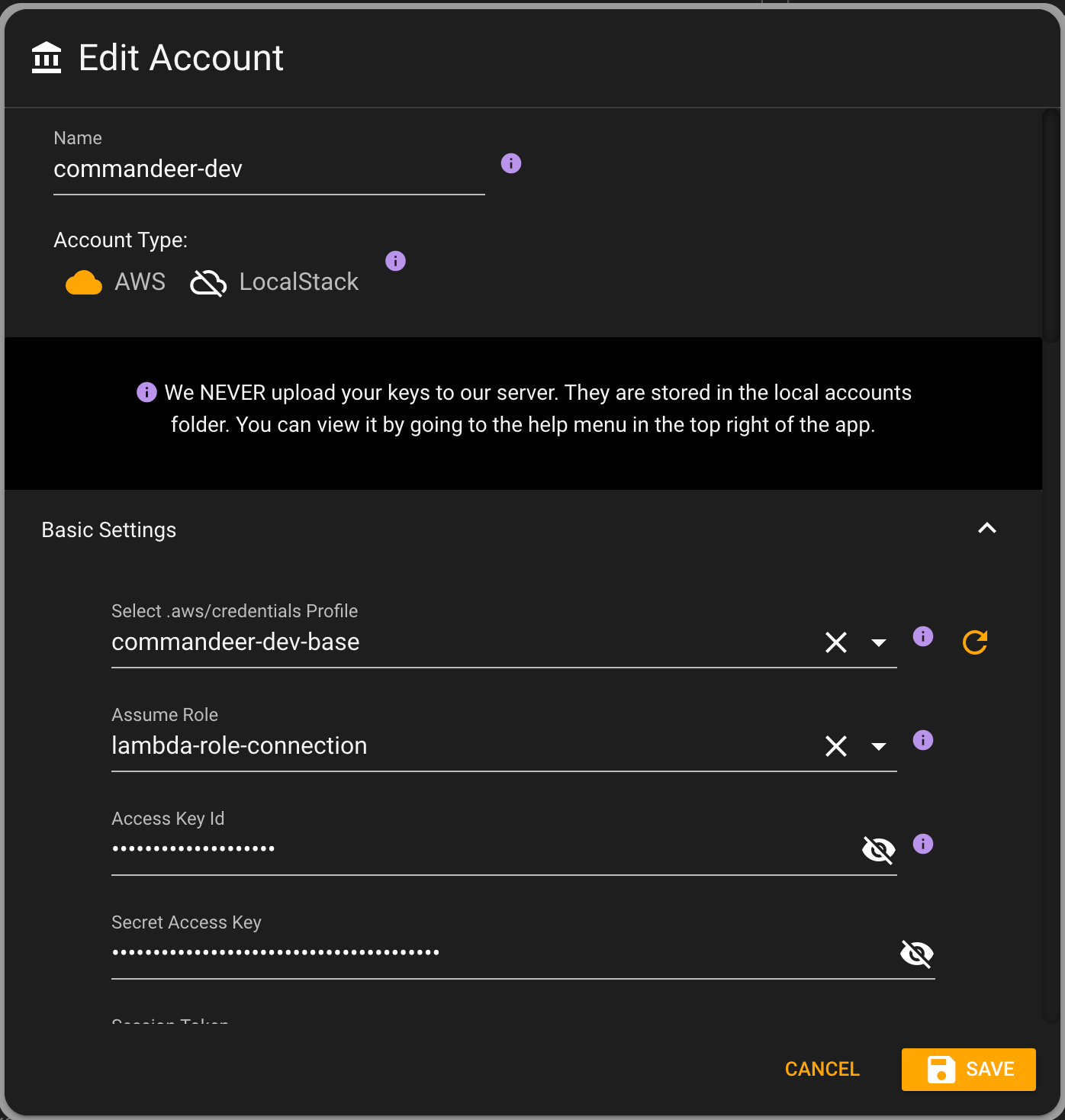
By selecting the top profile, it will automatically populate the keys. And if there are roles associated with the profile, then the assume role will be populated. Now, once saved, in the top of the app, you can see that now you are able to select a role to assume.
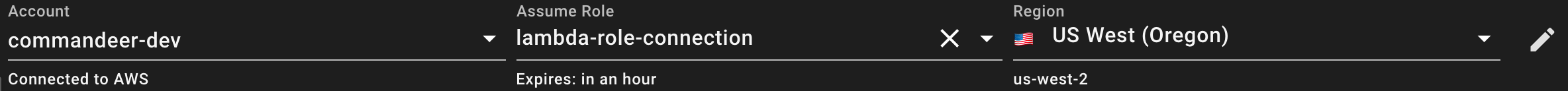
Under the hood, we use AWS STS (Security Token Service). It takes in your base keys, and the role arn you want to connect to, and then gives you back new keys, and a session token. These are short lived keys, so it also let's you know when they will expire.
You can view these all on the account detail page.
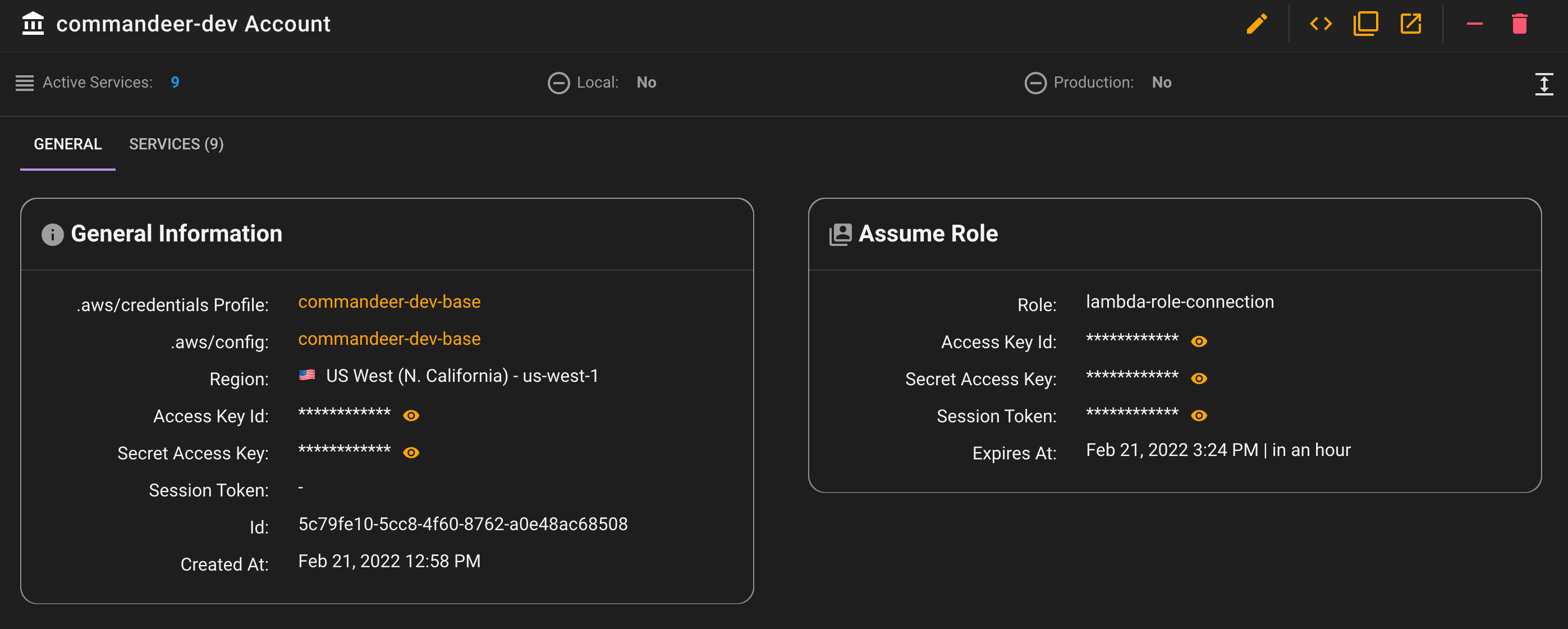
Now, all connections in Commandeer will use the assume role keys, and voila, you will be able to see your system.
# LocalStack Port Fix
There was an issue some users were experiencing with having a different port than 4566 for LocalStack. It turned out to be a race condition bug in the refresh of the system. This has now been resolved.
# Account Refresh
When you click the refresh button at the top left of the app, it clears your local cache, and go and retrieves your entire system (just the metadata) from AWS or LocalStack. Each service is queried in a separate promise. We now will show you the error that occurs if any when connecting, and they will appear in the notifications. Before we would just eat the error, and show you no data, but now with the assume role feature, this helps a bit in determining if a role can't access something.
# Conclusion
This release got a much needed feature for many of you out there. We are continuing down the path of version 3.0, but are excited to finally have gotten this out there for you!
