Using Assume Role to access AWS in Commandeer
# Using Assume Role to access AWS in Commandeer
The concept of assuming a role in AWS is pretty straightforward. You as a developer will have your IAM user with access keys, but this user will not have access to any resources. Your sysadmin will then give you access to different roles in the system. For instance, you might get access to a lambda role that allows you to view lambdas and the services they talk to like S3 or DynamoDB.
# .aws/credentials and .aws/config file
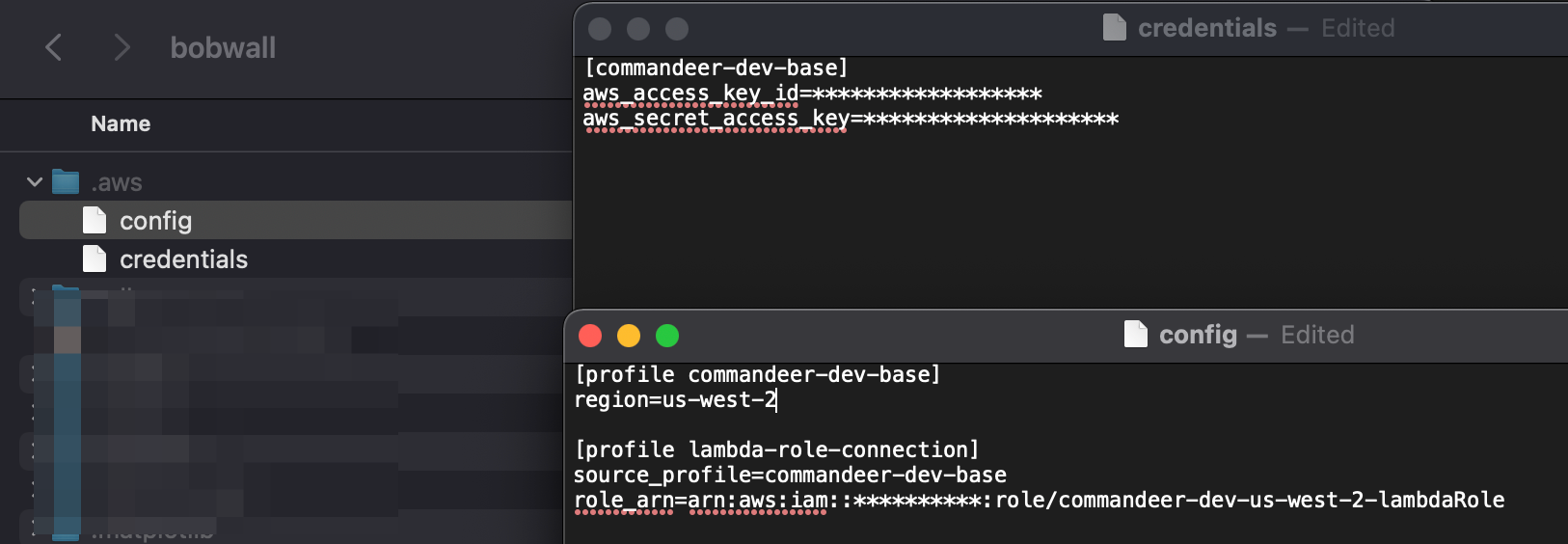
Your main user access keys need to be setup in the .aws/credentials file. In the top right of the image below, you can see that the name of the profile is commandeer-dev-base. This profile has the access and secret access keys to authenticate with. These are your base user keys. In the bottom section, you can see that there is a lambda-role-connection profile. This has a reference to commandeer-dev-base via the source_profile. It also contains the role__arn of the role you would like to assume. You may have many roles that you need to assume to check your system.
# Commandeer Account
In Commandeer, when you create an account to connect to your system, you will be able to select this main profile, and then the lambda-role-connection role as well. Below you can see the Edit Account dialog with these selected.
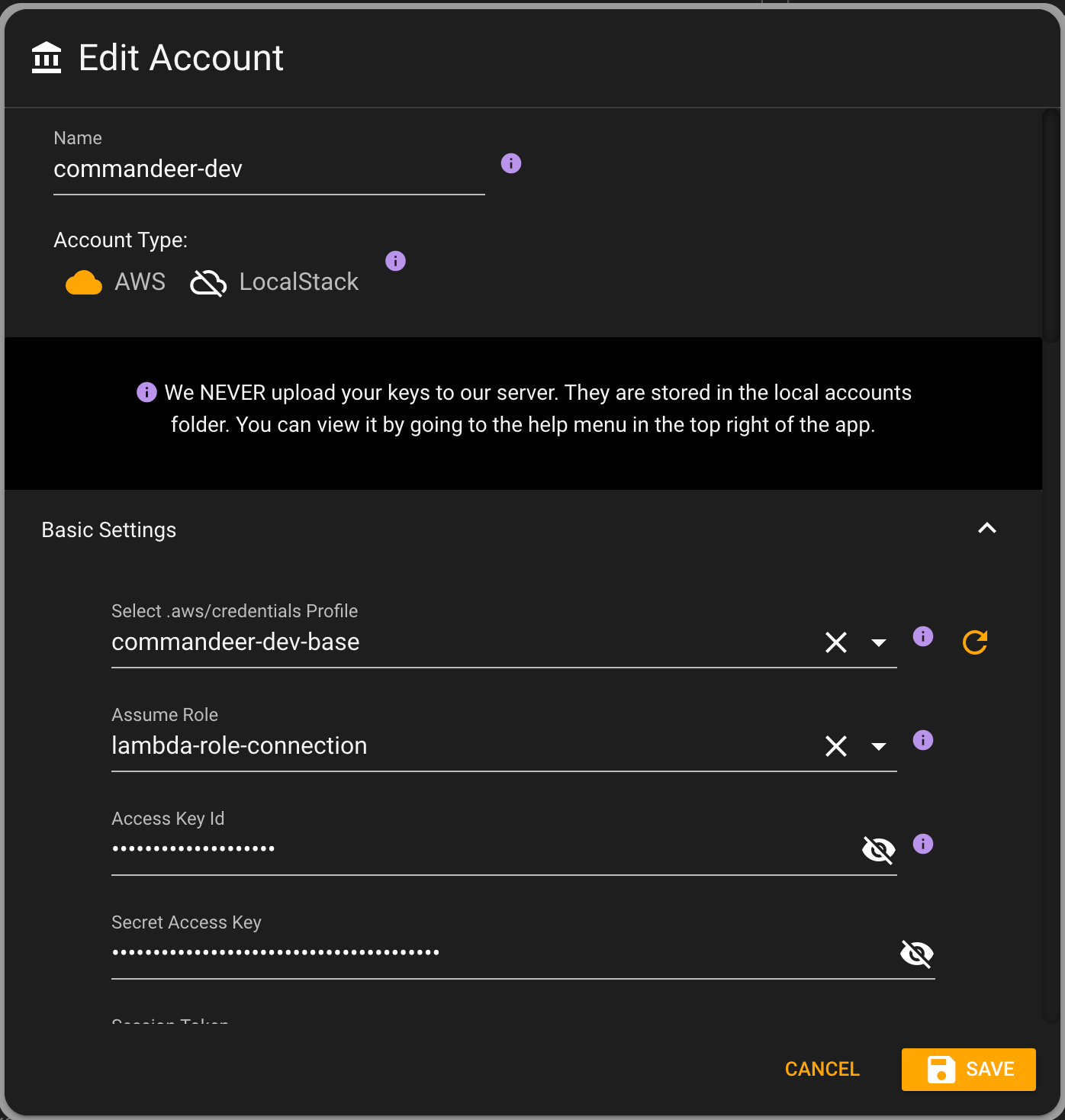
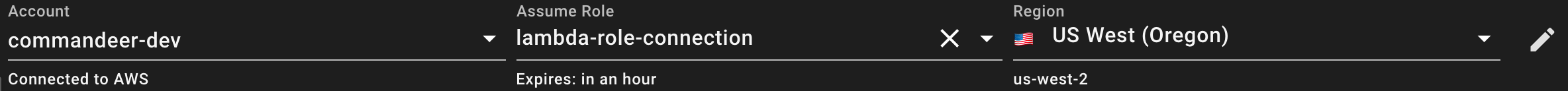
By selecting the top profile, it will automatically populate the keys. And if there are roles associated with the profile, then the assume role will be populated. Now, once saved, in the top of the app, you can see that now you are able to select a role to assume.
# AWS STS for Role Keys
Under the hood, we use AWS STS (Security Token Service). It takes in your base keys, and the role arn you want to assume, and then gives you back a short term set of an access key, secret access key, and a session token. These are short lived keys, so it also let's you know when they will expire. By default, these keys expire in an hour. You will need to press the refresh button in the top left of the app to refresh these keys.
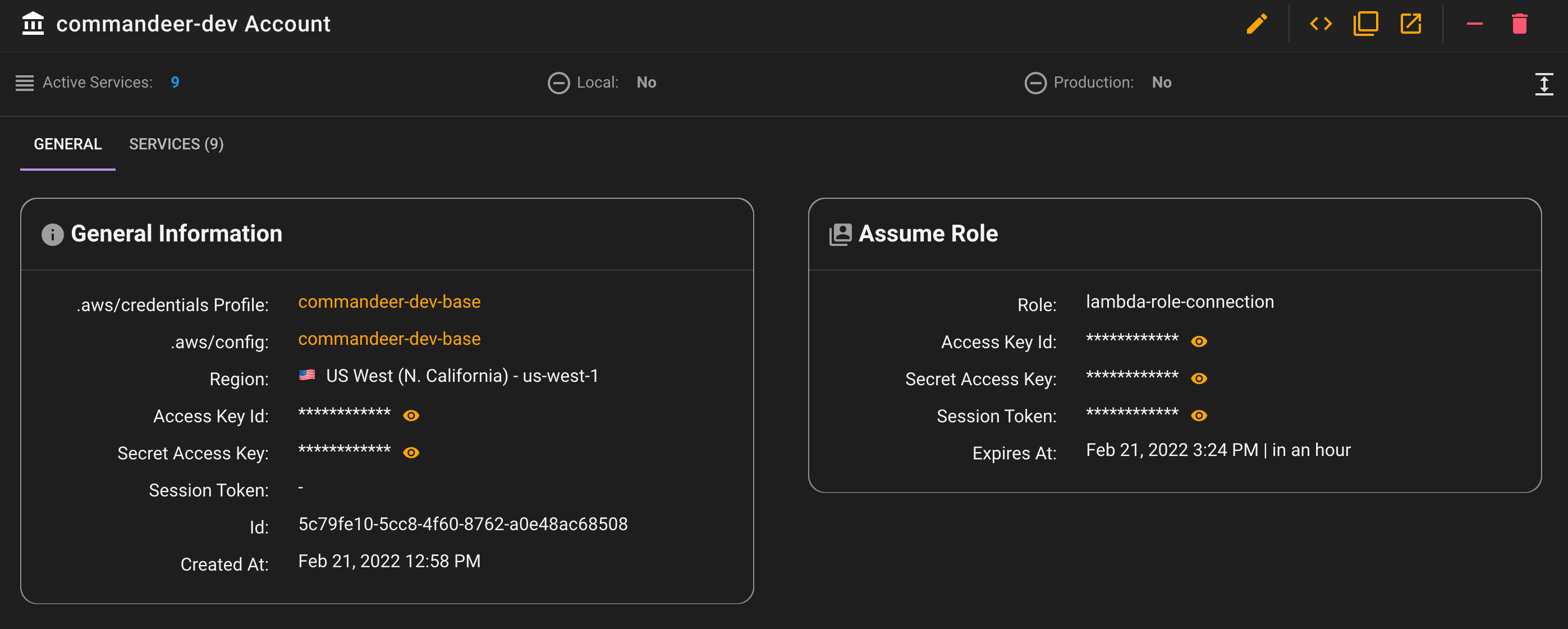
Below you can see a more detailed look into the account. On the left hand-side you can see the profile and config profiles it is using. On the right hand-side you can see the assume role and the current keys being used.
# Conclusion
If you are developing for a company, most likely you will have to use role based keys for accessing AWS. Commandeer can help with this tremendously by enabling you to view your system in a GUI. Your security ops team will rest easy knowing there aren't important keys out in the wild.
